Why it matters for the future of cybersecurity in your organization
As an InfoSec officer, you’re not sitting around twiddling your thumbs, so you may feel confident you don’t need to worry about SOC 2-compliant vendors. After all, you’re working hard every day to make sure your house is secure.
When your team is in the trenches, executing plans to shore up the crown jewels of your company, do you really need more cybersecurity products or to spend time double-checking that you’re using SOC 2 compliant vendors?
Actually, it’s quite important because a gap in vendor security can all too quickly lead to a vulnerability in your own security. It just takes one skillfully executed supply chain attack like the infamous SolarWinds hack.
What is SOC 2 compliance?
If you don’t know what a SOC2 report is, you’re probably not asking your current vendors to show you theirs or using it as a criterion for potential vendor selection. The quick explanation: SOC 2 is an auditing system designed to provide third-party confirmation of a certain level of security.
SOC stands for System and Organization Controls and the auditing system was developed by the American Institute of CPAs (AICPA). It outlines trust principles that help companies assess risk.
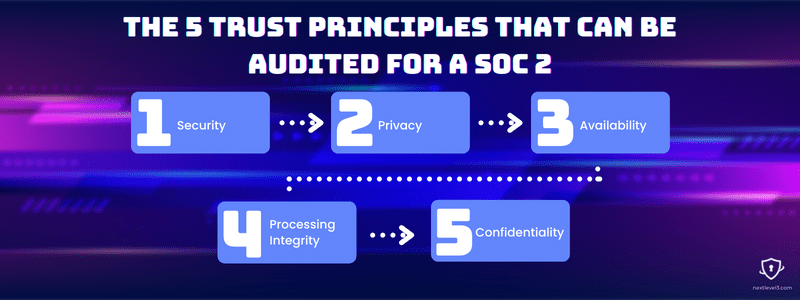
There are five trust principles that can be audited for a SOC 2 report, but only security is required. They are:
Security — how are systems and information kept secure?
Privacy — how is personal information obtained, secured, and destroyed?
Availability — how does an organization access others’ information as a third-party service?
Processing Integrity — how is system processing completed and authorized?
Confidentiality — how is confidential information secured?
For vendors to become SOC 2 compliant, there are a lot of measures and controls that need to be strategized, deployed, and tested. That requires a time and resource commitment. Once those controls are in place, a company can undergo a SOC 2 Type I audit.
After this test, a SOC 2 Type II audit monitors compliance at six- to twelve-month intervals, verifying that the systems continue to work over time. An audit costs tens of thousands of dollars on top of the cost of developing and implementing a comprehensive compliance plan.
By doing all the work of setting up, demonstrating, and verifying their security, when a company succeeds in its audit, it is showing a dedication to also maintaining the security of its clients — this is what you want to know during vendor selection!
Why SOC 2 is important to vet third-party vendors
Large enterprise companies have rigorous vendor management plans and generally only work with SOC 2 compliant vendors because it is the growing industry-standard in cybersecurity.
But it’s not only important for large companies to ensure their vendors are secure. Any organization that uses SaaS, cloud, or other kinds of network services should make sure their information is in the hands of reputable third parties that take the security of your information as seriously as you do.

It may seem sufficient, at first, to know that you’re working to make sure your company is secure and your vendors are working to make sure their company is secure. The benefit of a SOC 2 report is it adds a third, impartial attestation that objective security standards are being met and maintained over time.
It’s also important to differentiate whether the service you’re using is, itself, a SOC 2-compliant vendor. Some companies, when asked, will provide a report for their data center provider like AWS, Azure, or GCP, but have not been audited themselves. This is a start, but a fourth-party data center isn’t the only vulnerability.
How to conduct vendor due diligence
Once you’ve decided that it’s important to ensure that you’re using SOC 2-compliant vendors, you need to determine how to conduct due diligence during vendor selection. It’s also critical to maintain ongoing confirmation checks for existing vendors.
Here’s a basic strategy for putting due diligence procedures in place:
- Assemble a team — If you’re a large company, put together a whole team. Include anyone with relevant insight into InfoSec and compliance.
- List your current vendors — If you’re too small to need an entire team, at least compile all the third-party services your company is currently using.
- Who knows what? — Identify which vendors have access to networks and data and at what levels.
- Monitor current vendors — Once you’ve verified your company is working with SOC 2 compliant vendors, continue monitoring their status and performing security checks.
- Vet potential vendors — As you conduct future vendor selection, add SOC 2 Type II reports as a criterion for consideration.
Ensuring cybersecurity with SOC 2 compliant vendors
Every security measure in the world that your team rolls out across the company can be skirted if an attacker comes through the side door. Any vendors whose security standards are not up to your company’s standards will pose a threat to your information.
It is possible to perform a security audit yourself during your vendor selection process. But the SOC 2 auditing system exists for just that purpose, saving you time and energy. The fact that it’s carried out by a third party adds a layer of corroboration that neither you nor vendors can achieve on your own. Keeping a tight perimeter and protecting your company is your job and SOC 2 is an important resource to help you do that. Vetting vendor security is an important consideration for every cybersecurity officer.
